Page 1 of 1
User Log-in/Sign-in
Posted: Sun Aug 29, 2021 3:13 pm
by PavelChekov
Has anyone implemented a user log-in (ie: asking for a username and password), in their OSes? If so, how?
Re: User Log-in/Sign-in
Posted: Sun Aug 29, 2021 5:56 pm
by klange
Sure, I have both a graphical and a TTY-based login.
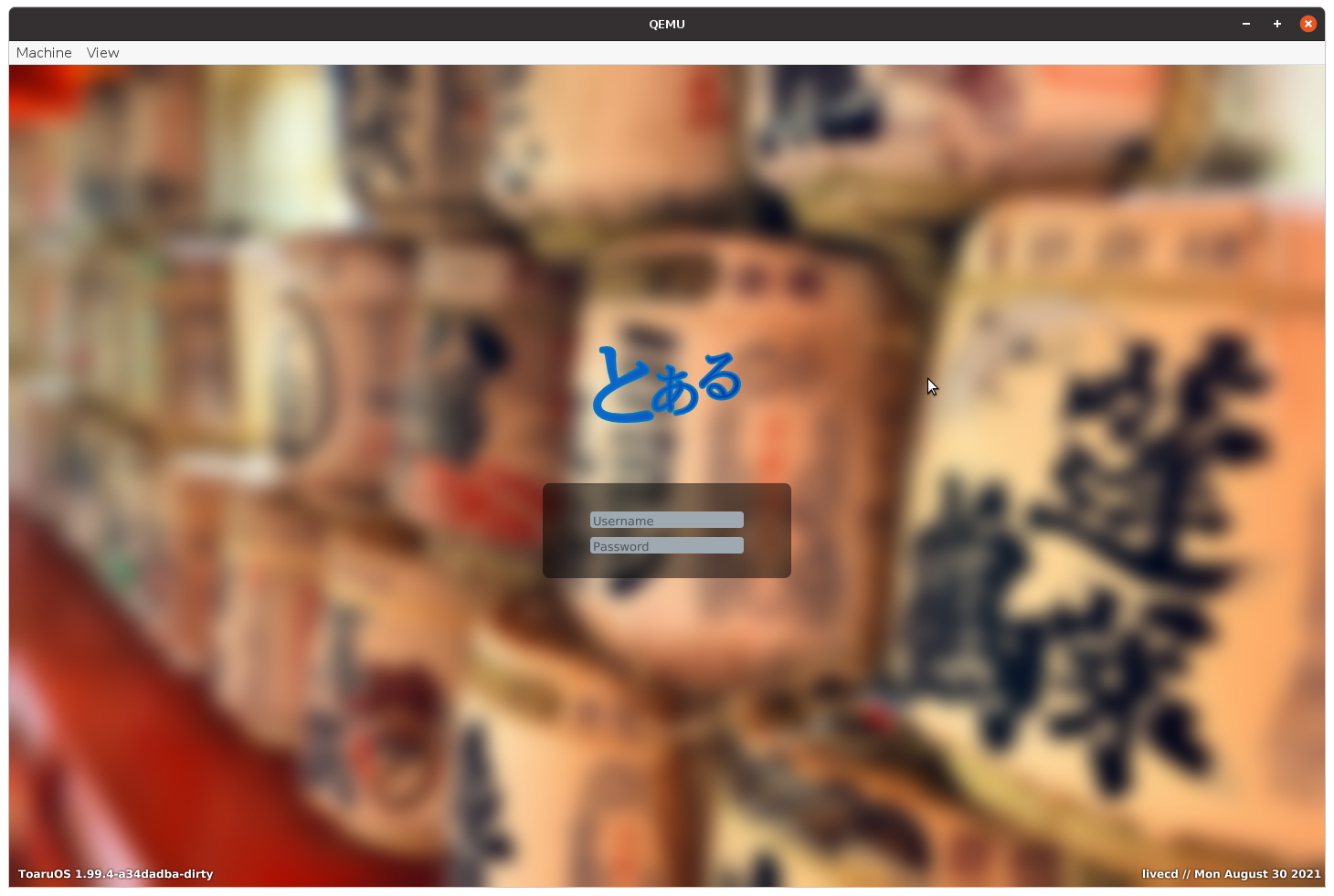
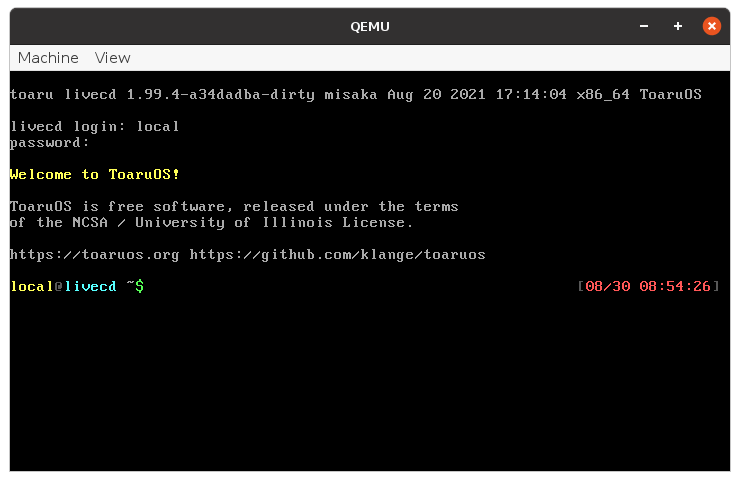
They both work the same way. They run with privileges to change users and access the authentication database, and they prompt for a username and password (be sure not to display the actual password as it's typed!), and if the authentication information matches, they fork, switch to that user, and run the relevant graphical or shell-based session. And when the user is done and their session ends, the process begins anew.
Re: User Log-in/Sign-in
Posted: Tue Aug 31, 2021 2:57 pm
by PavelChekov
Where do you store the passwords to check against?
Re: User Log-in/Sign-in
Posted: Tue Aug 31, 2021 5:55 pm
by thewrongchristian
PavelCheckov wrote:Where do you store the passwords to check against?
Traditional UNIX location is in /etc/shadow (read restricted to root processes) or /etc/passwd (not a good idea, /etc/passwd needs to be world readable.)
The password can also be stored over the network, and can be authenticated locally or remotely.
The point being, there is no single place to store passwords. Most UNIX like systems use Pluggable Authentication Modules (PAM) to implement authentication, so the location of the password storage becomes a function of the PAM plug-in.
Re: User Log-in/Sign-in
Posted: Tue Aug 31, 2021 6:43 pm
by Octocontrabass
Also, the password isn't stored. A hash of the password is stored, and the hash algorithm is chosen so that it should be difficult to figure out the password even if you know the hash.
Re: User Log-in/Sign-in
Posted: Tue Aug 31, 2021 7:06 pm
by klange
In classical Unixes the passwords
were stored... and then later they were stored in an encrypted (recoverable!) form.
I've intentionally stuck with actually storing passwords in plain text as a clear indicator that the security of my OS is lacking and should not be assumed, though I did previously use SHA256 hashes in the past.
On the note of authentication, this is something POSIX specifically does not cover, so even if you're aiming for standard compliance you're open to do whatever you want. I hide away my authentication process into
a library that has methods to verify credentials and assume an identity, and it gets used by
the login apps as well as
sudo.

